|
Form in FastAPI in Python Hello Folks! In this article, we are going to learn to create our first FORM using FastAPI in python. We are going to make use of python Jinja2Tempates to read the HTML page from a template folder. We are going to need to import Form and Request class from fastapi Make sure following modules are installed
We assume th ... Read more » |
|
Internet of Things (IoT) The Internet of Things (IoT) refers to the interconnected network of physical devices embedded with sensors, software, and other technologies to enable communication and collect data with other devices and systems over the internet. These devices range from ordinary household objects to sophisticated industrial tools. We are most likely to use IoT devices in our day to day life. Most common example is your Alexa device or your smart bulb or smart fan.
|
... Read more » |
|
Let's try to differentiate Power BI service and Power BI desktop: Power BI desktop is a desktop application which is mainly used by report developers to create reports, charts and graphs locally
Power BI service is a web based SaaS application which is used to create reports and dashboard online and present to decision makers and stakeholders directly via link or email.
Both have different purposes. Power BI service supports extensive data transformation using Query editor and DAX function where as in power BI service we have limited features to transform data. ... Read more » |
|
Today we are going to learn how to embed a power BI visualization to your website. I have created below charts and graph in my Power Bi Service account which I am gonna add or embed here:
Lets try and understand how we embed this to a website:
|
|
During your appraisal discussion with your manager, it's important to cover various topics to ensure a comprehensive review of your performance and progress. Here are some key areas to discuss with my experiences:
1. Accomplishments: Highlight your key achievements and successes over the appraisal period. Discuss any significant projects you completed, goals you achieved, or challenges you overcame. Provide specific examples and quantify your accomplishments when possible.
2. Goals Review: Review the goals you set in the previous appraisal period and discuss your progress toward achieving them. Identify any goals that were met or exceeded, as well as any goals that were ... Read more » Attachments:
Image 1
|
|
There are only four types of people in this world. I have categorized people into 4 types based on their knowledge and competency.
1. He knows that he knows These are the people of supreme quality. They are best aware of their knowledge and skills and very well know how to use them. They never face any problem as they use their information at right place and right time. They can tackle any situation as they apply the right remedy at right time for any or all types of situations. This class has the best decisive power which enables them to plan ahead for unforeseen circumstances. This category focuses on its strength and exploits its knowl ... Read more » |
|
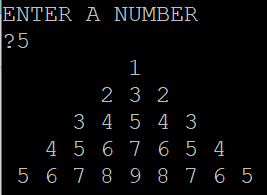
Dear readers we have an assignment to do where we have to print a pyramid of numbers. The user can enter a number as input and for that number as as range the pyramid of numbers should be printed.
So if the user enters 5, the number pyramid should look like this:
So we are going to write a proram to generate this pyramid pattern. Basically we are going to use FOR loop to achieve this. I have include the full tutorial here to create this program ... Read more » |
|
So, you worked hard day and nights to develop the codes, assignments and project slides and what not. And finally your boss shoots you down saying "You have not done well, the client is not happy at all ! Your performance is too week!!"
We all get criticized and pushed back at work in IT sector. And, the best part no matter how great job you have done, how many codes you have written, how many issues you have resolved, they all go unnoticed and if you make a very small silly mistake, that's where your lead and the entire hierarchy jumps into to make a speech..
|
|
Unibasic programming provides two ways to run programs or commands.
With UniData MENUS, you can transform the UniData command line interface into a menu driven interface. Menu driven option is a better option to run any command PROC or sentence in Unibasic. The advantage of menu driven : You can use a menu to support database security. For example, you can provide menus for users to access data entry programs and reports, while denying them access to the UniData prompt. All menus are stored in MENUFILE , each UV account usually has a MENU ... Read more » |